Initial iRODS Audit (AMQP) Rule Engine Plugin is released
We are happy to announce the release of the iRODS Audit (AMQP) Rule Engine Plugin. This release is the product of more than a year's worth of work to prepare the rule engine plugin framework and extensive testing with multiple message brokers across varying operating systems.
This release requires the recently released iRODS 4.2.2 and is already available in both the APT and YUM repositories hosted by RENCI. A prototype of this code used in December 2016 and demonstrated at TRiRODS a week later.
The Audit plugin has been tested with Apache ActiveMQ 5.13.2 and 5.14.1 and RabbitMQ 3.6.12 on Ubuntu 12, 14, 16, and CentOS 6 and 7. It uses the AMQP 1.0 standard to encode the messages, potentially for every policy enforcement point (PEP) that fires within the rule engine plugin framework. A PEP can be fired for every operation across every plugin type (e.g. database calls, network activity, resource/storage activity, etc.) and the generated AMQP message will contain the full context from the point of call. For example, with the default audit_.* regex configured, a basic ils will cause the Audit plugin to emit over 1200 AMQP messages, each containing actionable information about what part of the iRODS logic triggered that event. An iget will generate messages containing additional information about logical paths, physical paths, filesize and more.
The ability to gather, correlate, and interrogate messages from every operation means that a full audit (and very powerful reporting capabilities) become possible. The original demonstration used the following setup to build a dashboard of live activity within the iRODS Zone.
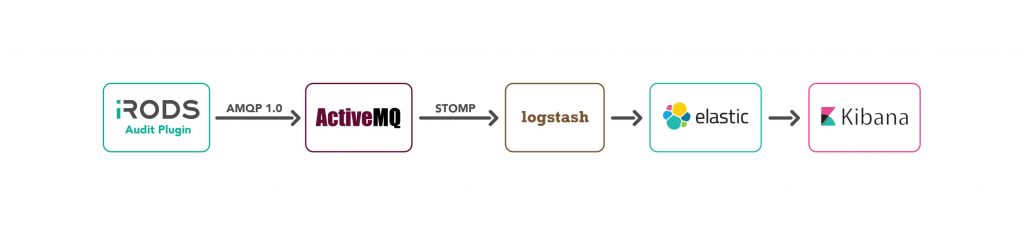
We demonstrated a few of these possibilities at the SC17 workshop in Denver a couple weeks ago.
We are very interested in hearing about the work you may do with this type of capability. We hope to see dashboards, standardized reporting, and security audits built from this real-time data coming from live iRODS servers.
Terrell Russell